Breaking Videogames
For those who can't play a video game without dissecting it
Project maintained by banyaszvonat Hosted on GitHub Pages — Theme by mattgraham
Quick update: we are in CRestore::SetReadPos, having been called from CSaveRestoreBlockSet::ReadRestoreHeaders:
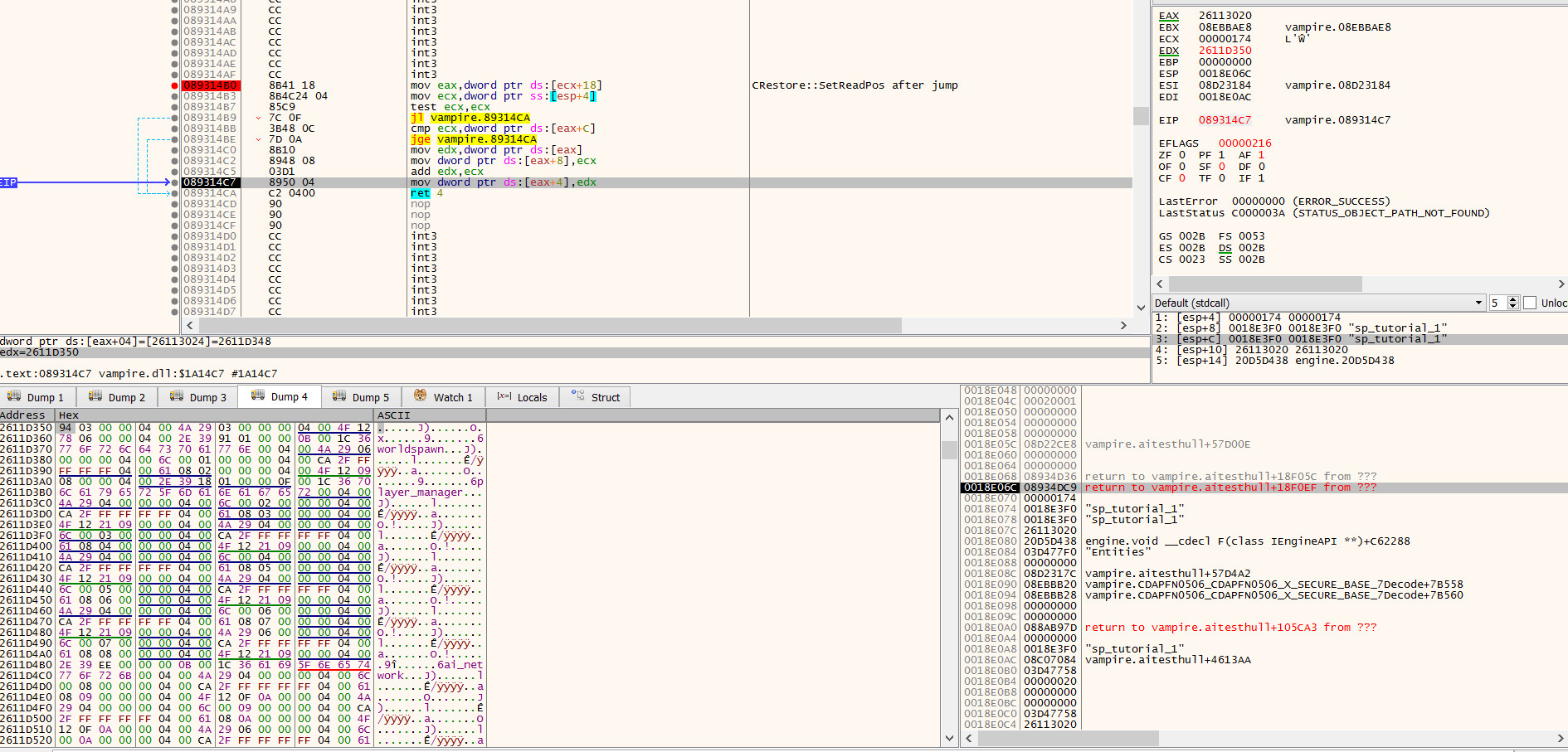
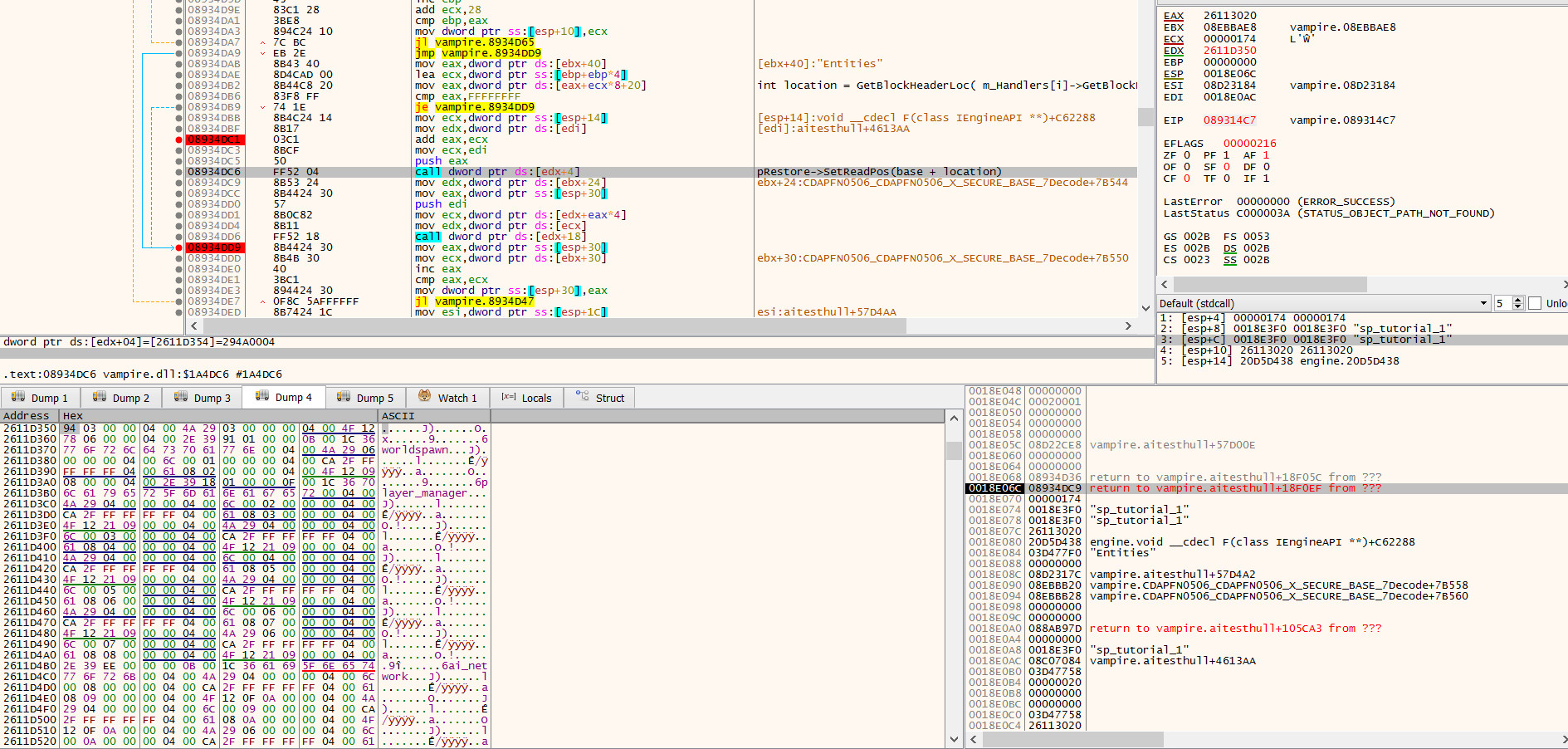
edx holds the location of the Entities block header in the in-memory buffer. In the hex dump on the bottom left, you can see this is between the Python and worldspawn strings from the previous post.
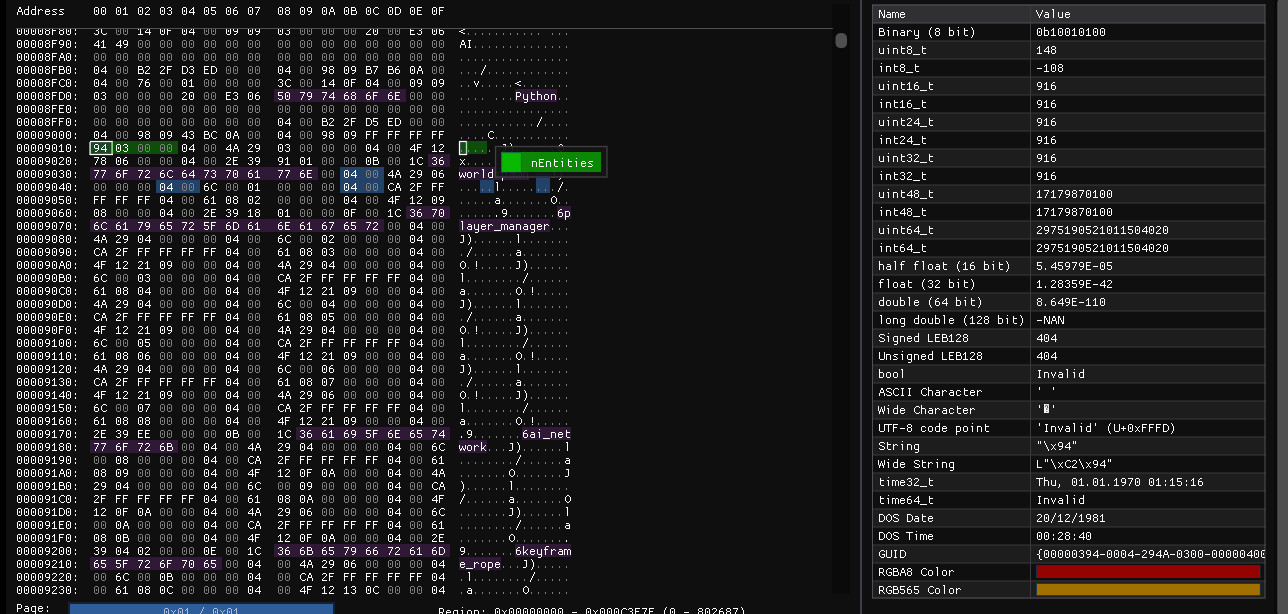
CEntitySaveRestoreBlockHandler::ReadRestoreHeaders tells us that the first field is an integer, nEntities:
The field in question is highlighted here in green, and according to this, we should expect 916 entities.
Counting the entries by searching the range 0x9000-0x17CEE[^1] for ASCII strings of at least 3 characters that start with 6 gets us…
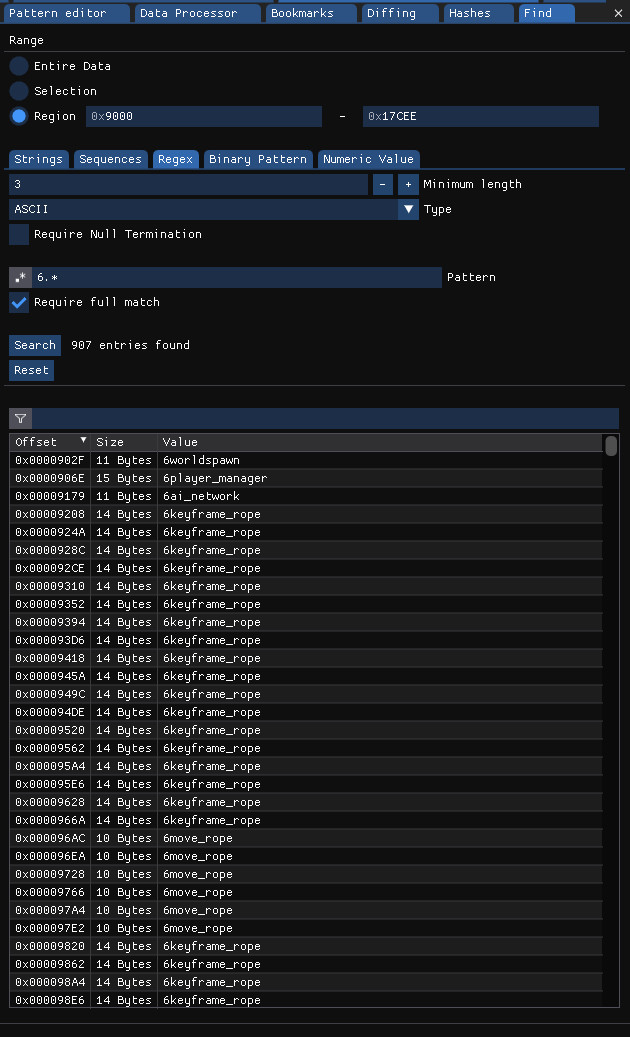
… 907 entries. Ehh, close enough.
This suggests a game plan for finding the Python data:
- Set a conditional breakpoint in
CSaveRestoreBlockSet::ReadRestoreHeadersto stop whenPythonis being passed toGetBlockHeaderLoc - Step through
CRestore::SetReadPosto get the header’s location in the in-memory buffer - Locate it in the unpacked save file
- Reverse engineer
CPythonSaveRestoreBlockHandler::ReadRestoreHeadersto see what fields it contains - To get the actual data, do the same with
CSaveRestoreBlockSet::CallBlockHandlerRestoreandGetBlockDataLoc
[^1] nEntities is at offset 0x9010 in the file, while the last string that falls into the pattern of starting with a 6 is at 0x17BF2.